梦回还

1.迷失之门ez
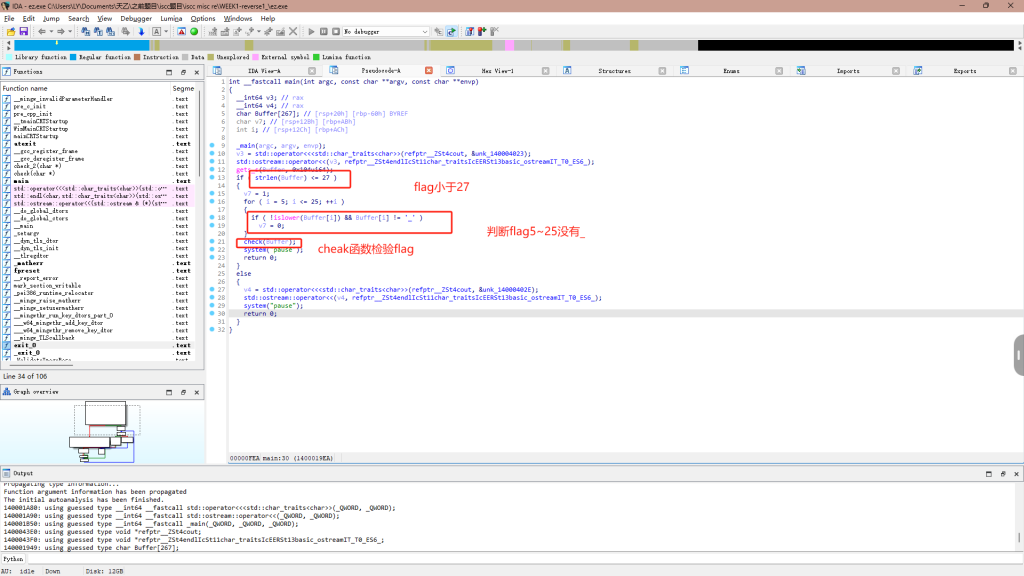
islower是检验小写的
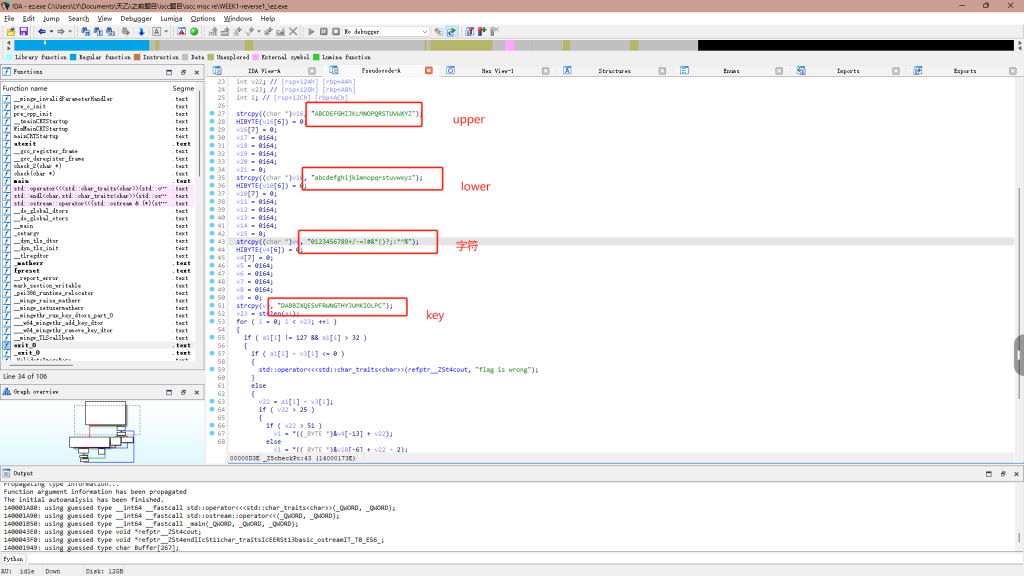
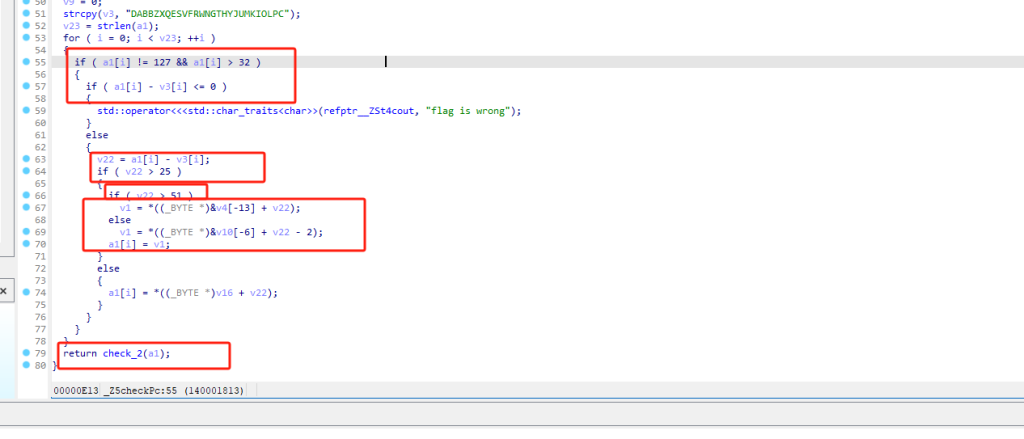
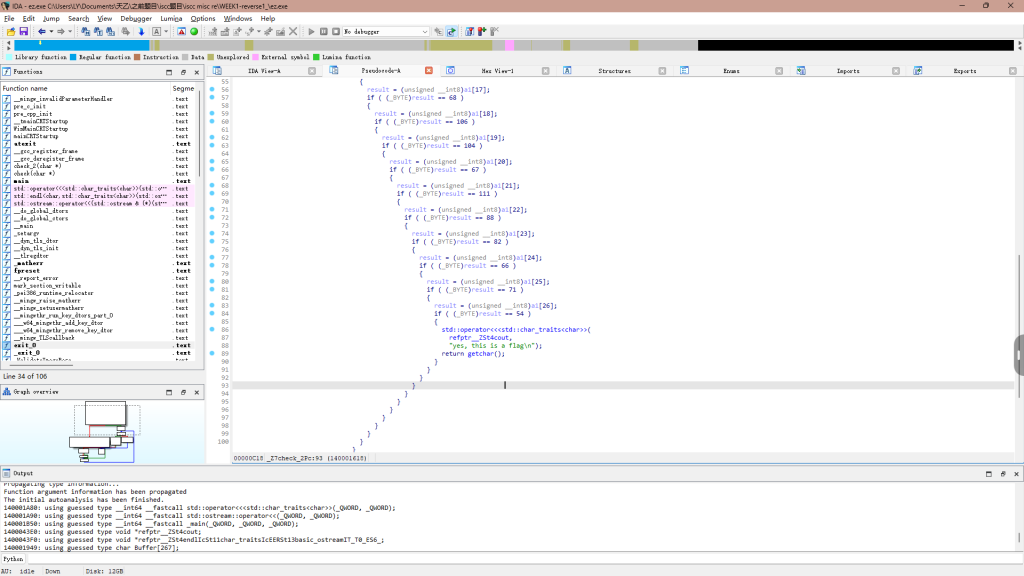
cherk2检验得到flag
Exp
encrypted_values = [70,83,66,66,104,75,115,113,113,81,103,100,81,99,49,109,71,68,106,104,67,111,88,82,66,71,54] #密文
enc = [chr(i) for i in encrypted_values]
def decrypt(s):
char_sets = {
"upper": "ABCDEFGHIJKLMNOPQRSTUVWXYZ",
"lower": "abcdefghijklmnopqrstuvwxyz",
"special": "0123456789+/-=!#&*()?;:*^%",
"key": "DABBZXQESVFRWNGTHYJUMKIOLPC"
}
decoded = []
for i, char in enumerate(s):
if char in char_sets["upper"]:
offset = char_sets["upper"].find(char)
decoded_char = chr(ord(char_sets["key"][i]) + offset)
elif char in char_sets["lower"]:
offset = char_sets["lower"].find(char)
decoded_char = chr(ord(char_sets["key"][i]) + offset + 26)
elif char in char_sets["special"]:
offset = char_sets["special"].find(char)
decoded_char = chr(ord(char_sets["key"][i]) + offset + 52)
else:
decoded_char = char
decoded.append(decoded_char)
return ''.join(decoded)
decrypted_text = decrypt(enc)
print(decrypted_text)
2.Cryptic.exe
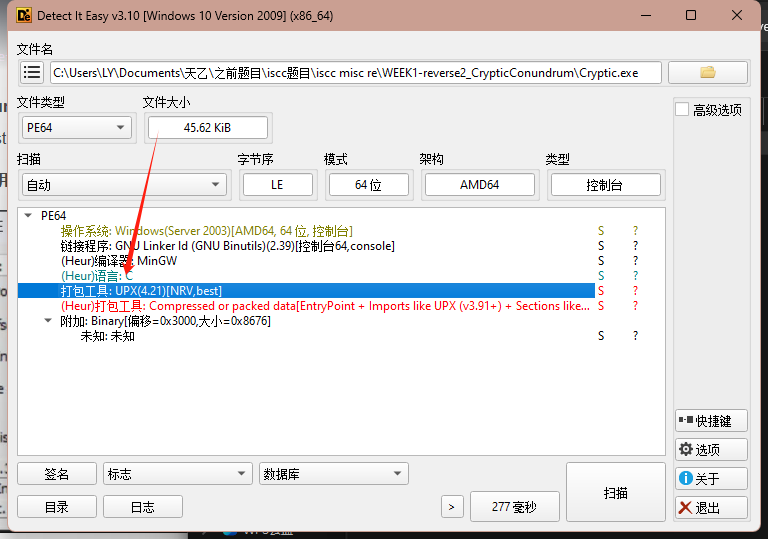
脱壳
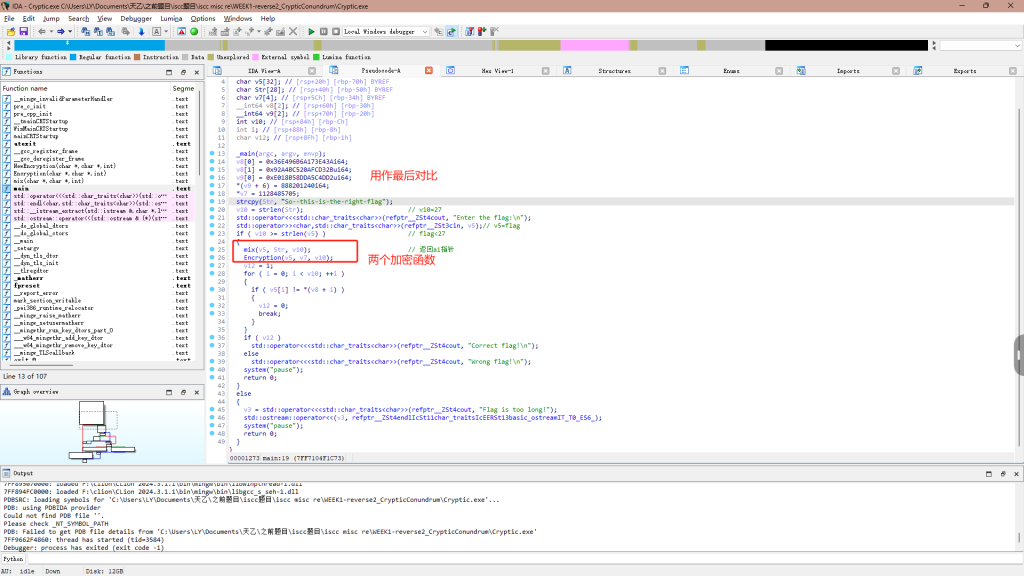
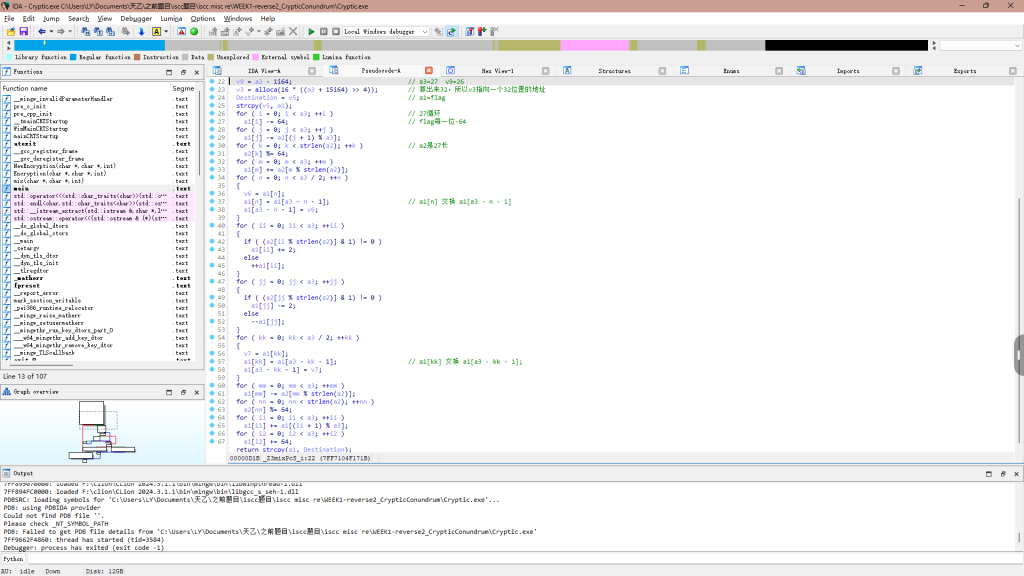
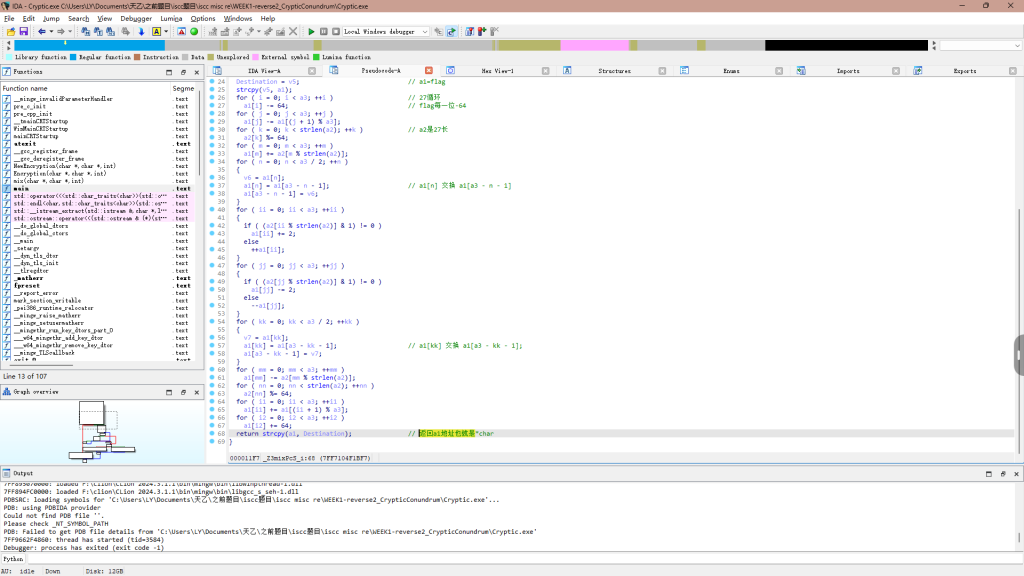
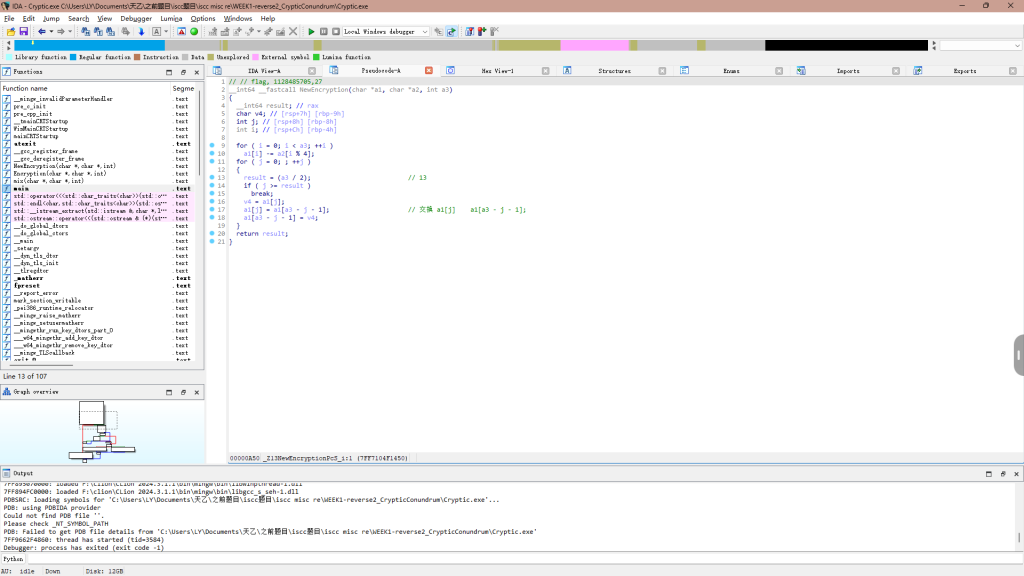
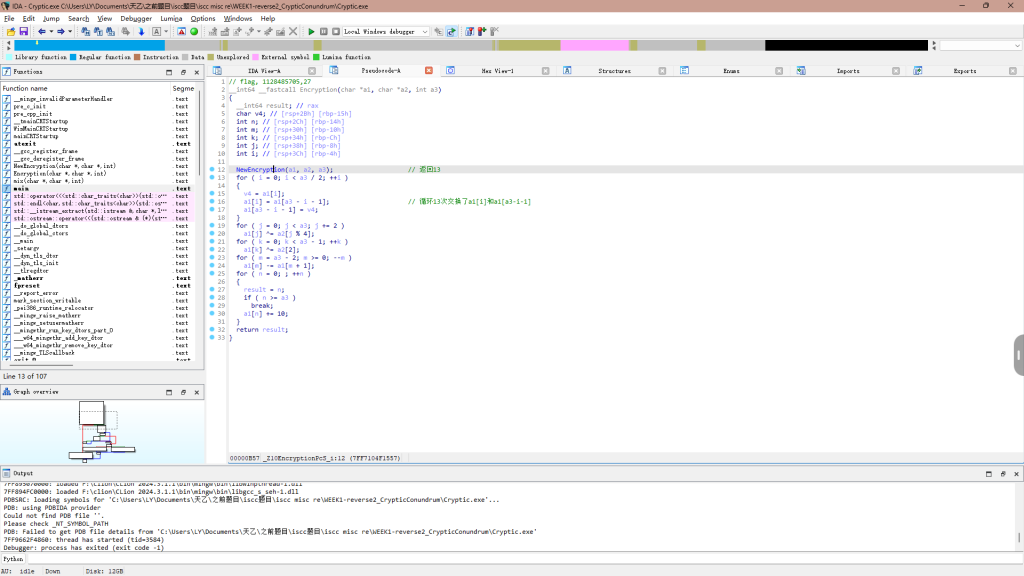
key在这
主要就是mix和Encryption这两个函数加密的
最后对比,分析过程再图中
def decryption(enc, key):
a3 = len(enc)
key_int = [ord(c) for c in key]
for n in range(a3):
enc[n] -= 10
for m in range(a3 - 1):
enc[m] += enc[m + 1]
for k in range(a3 - 1):
enc[k] ^= key_int[2]
for j in range(0, a3, 2):
enc[j] ^= key_int[j % 4]
for j in range(a3 // 2):
enc[j], enc[a3 - j - 1] = enc[a3 - j - 1], enc[j]
for i in range(a3 // 2):
enc[i], enc[a3 - i - 1] = enc[a3 - i - 1], enc[i]
for i in range(a3):
enc[i] += key_int[i % 4]
def main():
key = "ISCC"
enc = [0x34, 0xEA, 0x6D, 0xA7, 0xB0, 0x9C, 0x30, 0xE4, 0x7B, 0xC8,
0xEB, 0x2C, 0x8F, 0x8A, 0x40, 0xB5, 0xA0, 0xAE, 0xC3, 0x50,
0x07, 0xEE, 0xE5, 0x62, 0xF4, 0x34]
decryption(enc, key)
print("".join(chr(i % 256) for i in enc))
if __name__ == "__main__":
main()
3.Badcode
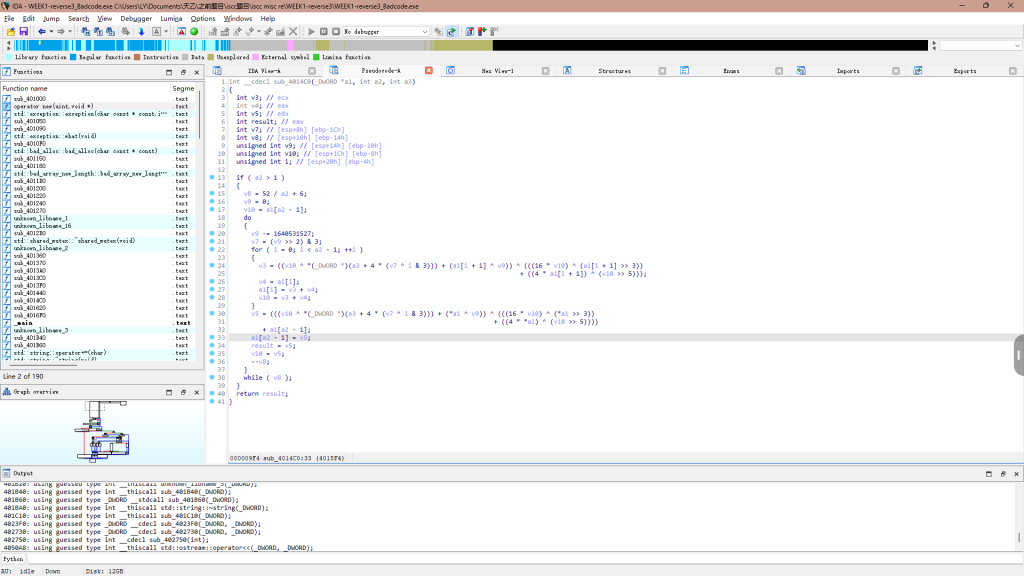
明显xxtea
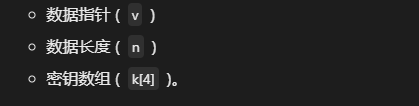
分析一下就是
sub_EE14C0(Buf1, 6, (int)&unk_EE7018);
这里buf1是加密数据
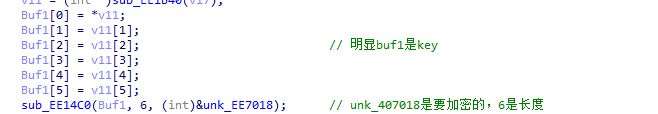
6是长度
unk_EE7018是key存放地方
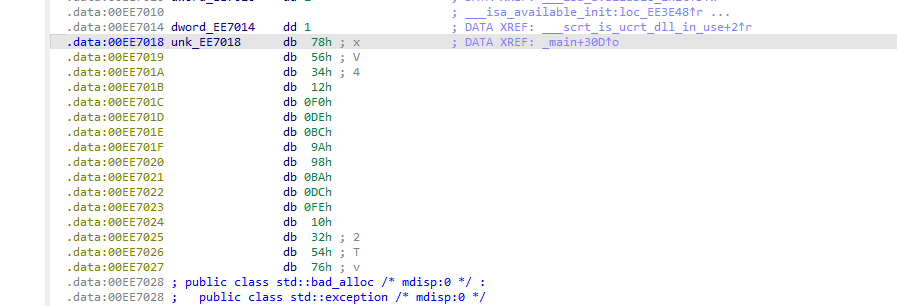
#include <stdio.h>
#include <stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
#include <iostream>
using namespace std;
void btea(uint32_t *v, int n, uint32_t const key[4]) {
uint32_t y, z, sum;
unsigned p, rounds, e;
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do {
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--) {
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
int main() {
uint32_t key[4] = {0x12345678, 0x9ABCDEF0, 0xFEDCBA98, 0x76543210};
uint32_t v[] = {0xE9E4F557,
0xD4988D1A,
0x9DC89258,
0xD50B9B4C,
0x3601727B,
0x91FEF8D1
};
btea(v, -6, key);
string xxtea = (char *)v;
int v16[24];
srand(0x18);
for (int i = 0; i < 24; ++i ) {
v16[i] = rand() % 10 + 48;
}
for (int k = 0; k < 24; ++k ) {
xxtea[k] ^= (v16[k] - 48);
}
for (int j = 0; j < 24; ++j ) {
if ( j % 2 ) {
xxtea[j] -= 2;
} else {
xxtea[j] += 3;
}
}
for (int i = 0; i < 24; i++) {
cout << (char)xxtea[i];
}
}

评论(0)
暂无评论